How to Bypass Firewall Using Nmap
The attacker need only. Nmap scans with the option -f in order to bypass packet inspection of firewalls so that packets can be encrypted while it sits idle in idle mode.

Nmap Firewall Detection Ack Probing Youtube
In this recipe we will learn some of the ways we can bypass firewalls.

. Which Nmap Scan Is Used To Bypass The Firewall. I use all of needed arguments to bypass its firewall but it doesnt answer. People could access all of their home systems from work changing the climate.
A machine known as Para was used to conduct SYN and ACK scans in ACK Scan. As well as scanning firewalls Nmap also provides port state information that allows the user to sneak past themA technique such as FIN scans can be used to accomplish the taskYou were shown scanresults against a machine the Para machine as part of the section called ACK Scan. Up to 5 cash back Bypassing firewalls with Nmap.
Any decent firewall book emphasizes this cardinal rule. Answer 1 of 3. Example Usage nmap --script firewall-bypass nmap --script firewall-bypass --script-args firewall-bypasshelperftp firewall-bypasstargetport22 Script Output Host script results.
Nmap Decoy Scan Bypass Firewalls What Is Firewall Bypassing Firewall using NmapHello everyoneIn this video we are going to see various techniques to b. While mapping out firewall rules can be valuable bypassing rules is often the primary goal. Can Nmap Bypass Firewall.
Many Internet pioneers envisioned a global open network with a universal IP address space allowing virtual connections between any two nodes. Can Nmap Bypass Firewall. A machine that goes by the name Para was used to run SYN and ACK scans in a section known as ACK Scan.
Set a specific MTU of the packets. Most of the time during a pentest we will come across systems protected by firewalls or Intrusion Detection Systems IDS. The Nmap provides different ways to bypass these IDSfirewalls to perform port scans on a network.
Individual techniques each have a low probability of success so try as many different methods as possible. All 1000 scanned ports are filtered Firewall rules allow file and printer sharing plus some other ports. Fragment Packets Nmap.
A flooded list of decoy addresses appears on log files. Capture a fragment packet. Nmap from beginner to advanced has covered many basic concepts and commands and in this second part of this series of articles I will discuss.
Unfortunately those are common. Nmap implements many techniques for doing this though most are only effective against poorly configured networks. Nmaps scan features provide an interesting combination of methods for sneaking through firewalls as well as obtaining desired port state information but without needing to block or disable firewalls.
Nmap --scriptfirewall-bypass --script-args firewall-bypasshelpervaluefirewall-bypasshelperportvalue Firewall-bypass NSE Script Example Usage. Nmap evade firewall and scripting updated 2019 Nmap is the most powerful scanner that is used to perform so many functions including port scanning service detection and even vulnerability detection. This allows hosts to act as true peers serving and retrieving information from each other.
With Nmap youll be able to sneak past firewalls while still finding information regarding ports in the desired status. Nmap -e eth0 -Pn --data-length 5 --badsum -g 80 -S 1921681103 -f -T1 -D 1921681200192168130192168145192168190 1921681102 This is the response. In this recipe we will learn some of the ways we can bypass firewalls.
In addition to scanning through firewalls Nmap enables users to obtain port state information despite a pass through. A technique like FIN scan may be used. Most of the time during a pentest we will come across systems protected by firewalls or Intrusion Detection Systems IDS.
Block and Slow Nmap with Firewalls. _ Firewall vulnerable to bypass through ftp helper. The capabilities of Network Access Point give you the option of scanning over a bridge without sharing the desired port state information.
In addition to FIN scans there are other techniques available. Techniques like FIN scan are part of this group. But any site can be accessed through the application so sensitive and unencrypted information.
How To Bypass Windows Firewall Using Kali Linux. What Does It Mean To Bypass A Firewall. One of the best defensive measures against scanning is a well-configured firewall.
Bypassing firewalls with Nmap. NMAP is basically a information gathering tools to collect network and system information it has several other use like to find out the IP address open port system details server version and other network vernability. Scanning with decoy addresses.
This script detects a vulnerability in Netfilter and other firewalls that use helpers to dynamically open ports for protocols such as FTP and. Nmap -sS -T5 192168112 --script firewall-bypass. Koenig Solutions offers IT Security training courses.
Browse blocked websites with no connection needed. Koenig certifies individuals in various information security and e-business skills. The Nmap provides different ways to bypass these IDSfirewalls to perform port scans on a network.
SYN and ACK scans of a robot named Para ran against each other in an ACK Scan subsection called ACK Scan. If not using the helpers default port. Executing an Idle Scan.
Also modern host firewalls also allow for processprogram exceptions so its possible that during the installation of nmap the installer added a process exception for itself to the windows firewall allowing itself to bypass other rules. In other words the FIN system is a kind of scan. To use these script arguments add them to the Nmap command line using the --script-args arg1valuearg2value syntax.
Follow this answer to receive notifications. Connecting Firewall Log File to Wiper Log Files Idle Scan. Use Tor to bypass a firewall.
Rather than simply obfuscate the network configuration as some techniques described later do well-configured firewalls can effectively block many avenues of attack. Can Nmap Bypass Firewall. FirewallIDS Evasion and Spoofing.
What Are Some Nmap Scan Options To Bypass Firewalls And Ids.
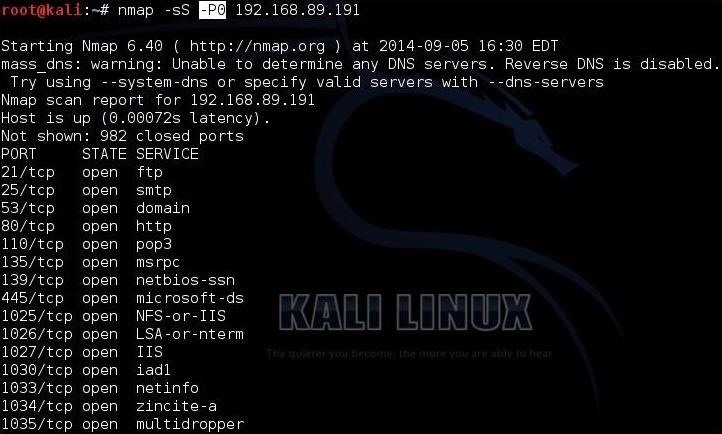
Hack Like A Pro Advanced Nmap For Reconnaissance Null Byte Wonderhowto

Bypassing Firewall Using Nmap Youtube

Evading Firewalls And Ids Using Nmap In Kali Linux 1337pwn

How To Bypass Firewall Using Nmap
![]()
Various Ways Of Scanning To Bypass Firewall Blog Securium Solutions

Understanding Guide To Nmap Firewall Scan Part 2 Hacking Articles

Bypassing Firewall Using Nmap Youtube
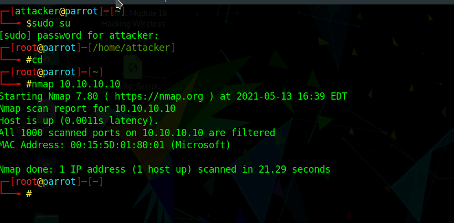
Project Bypass Firewalls Using Various Evasion Techniques By Takahiro Oda Medium
![]()
Various Ways Of Scanning To Bypass Firewall Blog Securium Solutions
Myitdiary Nmap Bypass Firewall
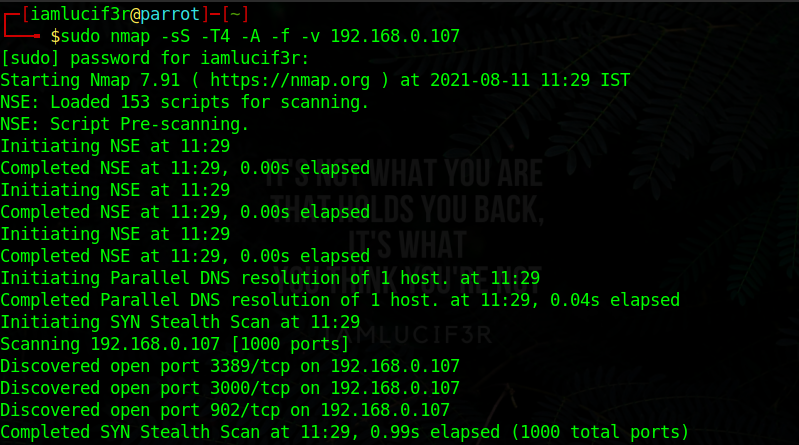
Top 10 Firewall Ids Evasion Techniques By Anmol Singh Yadav Medium

9 Nmap Decoy Scan Bypass Firewalls What Is Firewall Bypassing Firewall Using Nmap Youtube

Technology Redefine Ids Ips And Firewall Evasion Using Nmap
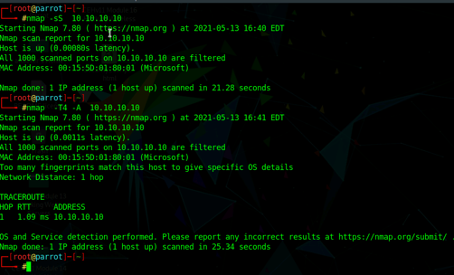
Project Bypass Firewalls Using Various Evasion Techniques By Takahiro Oda Medium

Understanding Guide To Nmap Firewall Scan Part 2 Hacking Articles



Comments
Post a Comment